Published November 29 2022
The word “cyber” refers to all things related to computers, information technology, and virtual reality. It includes the technology and processes designed to protect networks and devices from data breaches, identity theft, damage, and unauthorized access. Cybersecurity awareness is important for organizations as well as personal use (devices such as phones, computers, and tablets.) It is also important for the military, hospitals, as well as large and small corporations. Understanding cybersecurity, implementing defensive and offensive cyber protocols, and practicing continued diligence in staying up to date are all essential. Staying cyber secure starts with you.
Why is cybersecurity so important?
Proper use and knowledge of cybersecurity helps your organization and home create or maintain a defensive posture against cyber-attacks and breaches. These include unauthorized access, unauthorized deletion, and unauthorized modifications. This same proper use and knowledge helps prepare your organization or home offensively in the case of an attack or breach. It is important to realize that not all breaches, attacks, or threats come externally (although a majority do). Some incidents may originate internally, with either malicious intent or incidents that occurred inadvertently. Everyone within an organization and in your home is responsible for cyber safety. Cybersecurity safeguards your systems, computers, and data from attacks that can lead to interruptions in services, information theft, or exposure of personal information
What are the main aspects of cybersecurity?
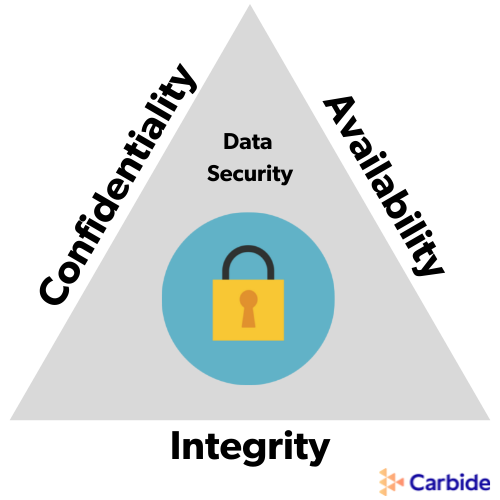
There are three pillars to cybersecurity, known as the CIA Triad. The three components stand for confidentiality, integrity, and availability. These are fundamentals when building your cybersecurity strategies.
- Confidentiality – Only authorized parties have access to your sensitive information and functions.
- Integrity – Only authorized individuals may alter/add/remove sensitive information or functions.
- Availability – Systems, functions, and data must be available on demand based on pre-determined, agreed-upon parameters.
What are the most common types of cyber-attacks or threats?
- Ransomware – Software that blocks access to a computer system. Without access to your files, the ransomware designer will ask for a ransom to be paid to unlock your files so you regain access.
- Malware – Software that interferes with your computer’s normal functioning. These are viruses, trojans, or other malicious programs that infect your system or network. They may disrupt or damage your computer system or allow for unauthorized access to confidential information.
- Phishing – The attempt to steal confidential information (credit card numbers, passwords, log-in information) through the use of email or other electronic communication forms. Typically, these appear to come from a reliable source.
- Social Engineering – A manipulation technique used to exploit the human error factor in cybersecurity. The goal is to steal private, personal, and financial information.
- Denial of Service (DoS)/Distributed Denial of Service (DDoS) – Attacks that are intended to make an online service unavailable to its intended users on the internet.
- Man in the Middle Attacks (MitM) – Communication where two parties believe they are talking with each other but a ‘man in the middle secretly intercepts the information. The attacker controls the conversation and relays messages between the two parties.
- Cross-site Scripting Attacks (XSS) – Malicious scripts are injected into the code of a trusted website or application. The malicious link appears enticing and is clicked on by a user. This allows for code injection.
- SQL Injection Attacks – Malicious SQL code is injected into an application allowing for backend database manipulation that provides access to confidential information.
Interesting fact: Injection attacks, which include XXS and SQL attacks, were the third most serious web application security risk in 2021.
What are the best practices to strengthen your cybersecurity?
Everyone within an organization and in your home is responsible for cyber safety. Increasing the cybersecurity awareness of all your employees or family members is critical. Creating, following, and updating your cybersecurity policies is key. Good cybersecurity involves multiple layers of protection using a combination of technology and best practices. Putting these practices in place does not guarantee you will avoid all attacks and threats.
This starts with good preventative solutions. Install antivirus and firewall software. Download patches and updates regularly. Do take the time to know and understand what it is you are downloading before you click ‘install’. As an employer, know your network, who is on it, and what access they have been granted. Control and monitor cyber activity. Requiring strong credentials and having clear policies (for example, requirements for passwords that is known to all staff) sets the tone and stage for stronger cybersecurity. Create and follow workplace cyber policies such as Acceptable Use, Data Classification, Data Security, and Data Destruction.
At both work and home, passwords should be unique for different login credentials. At home, make it a habit to monitor your bank and credit accounts regularly. Frequently back up your data so that you have the most recent data and information possible in the case of a breach or attack. Be intentional online. This is very important with social media use. If you would not write something on a postcard and mail it, then do not put it on social media. Never post about traveling while you are traveling.
Hint: you can back-post information or photos you do want to share on social media. These posts can play out, one day at a time, as if you were traveling but when you are back in your home and at work.
How can I teach myself or gain more knowledge in cybersecurity?
There are many options throughout Montana. These include in-person, online, asynchronous, and rapid training program options. Individuals may take an introductory course to learn about cybersecurity, work towards a Certificate of Technical Studies, or pursue further higher education opportunities and degrees. Online options are available for work teams or individuals, including Security Awareness Training and Workforce Development. If you are in sixth grade through adulthood, CyberMontana offers learning and training opportunities for you.
Keep Montana Cyber-secure
Cybersecurity awareness and in-house cybersecurity strategies are necessary best practices for any business or household. An array of options and opportunities are available to assist you in your cybersecurity growth. The first step is to define your need (awareness training, career opportunities, developing your workforce, a need for resources, or a need for incident response.) The second step is to do some research. The resource that is right for you is out there. CyberMontana does provide a variety of leads on our website, with the goal of continuing to add more statewide opportunities already available in the state. Consider your options (local/remote/in-person/online). Do a search that meets your needs. If you need help defining those needs, you may always contact us and we will connect you with the right resource in Montana.
Sources:
- https://www.simplilearn.com/tutorials/cyber-security-tutorial/cyber-security-for-beginners
- https://bootcamp.ku.edu/blog/the-beginners-guide-to-cybersecurity/
- https://blog.hubspot.com/marketing/cybersecurity
- https://www.techtarget.com/searchsecurity/The-ultimate-guide-to-cybersecurity-planning-for-businesses
- https://medium.com/edureka/what-is-cybersecurity-778feb0da72
- https://www.dhs.gov/science-and-technology/cybersecurity-resources
- https://niccs.cisa.gov/cybersecurity-career-resources/additional-resources
- https://sitsd.mt.gov/Cybersecurity/Resources/
- https://westoahu.hawaii.edu/cyber/cscc/global-cyber-environment/global-cybersecurity-resources/
