Published December 30 2024
Many organizations offer their employees the opportunity to work remotely, whether at home, in a coffee shop, or in a conference room. Working remotely comes with flexibility. It also comes with responsibility. Let us share a story about Joe.
Joe works for a technology company; managing contracts, overseeing operations, and reviewing sensitive information. However, he doesn’t know much about cybersecurity.

To avoid a cold and snowy commute, he decides to work from home one winter day instead of traveling to the office. Joe logs onto his home office and starts the day reviewing communications from a client. To do this, he uses his home internet network to log into his work accounts. This is the same browser profile used for personal browsing activities, such as shopping or watching the football game last night. After signing into his accounts, which all use the password “password,” Joe starts reviewing communications from the client involving their confidential marketing and project development plans.
By lunchtime, the roads have been plowed and Joe decides to relocate to a nearby coffee shop for the rest of the day. After getting lunch and a cup of coffee, he sits at his favorite table in the middle of the shop. He connects his laptop to the shop’s open guest network, which doesn’t require a password. Once logged into his accounts again, he writes a response to the client and communicates their needs to his team.
Later in the afternoon, Joe reviews and approves contracts for another project and logs into the company accounts to check that a payment has been processed. At the end of the day, Joe shuts down his laptop and heads home to make dinner, contented with his convenient day of working remotely.
What Joe doesn't know is that his actions may have exposed his company, their clients, and their accounts to a wide range of cybersecurity threats.

Joe’s mistakes began early when he logged into his accounts from his browser profile. This might allow a cyber threat actor who has hacked into Joe’s browser in the hopes of finding his credit card information or personal details to also access a treasure trove of login information for his work accounts and confidential information from his company’s clients. This becomes more likely since his home network and computer are not monitored or maintained by his company’s IT department, increasing the chance that there may be threats or malware on his devices that can help steal company information.
Joe’s security is compromised because he uses the same password for all his accounts. "Password" is easier to hack than a more complex password or passphrase. Once a hacker defines this for one account, they can access all the accounts and systems Joe has access to with this password. This expands the security breach, spreading it widely across the company’s systems when it could have been contained to one account if Joe used different passwords for each one. Although it can be harder to create and remember different passwords for each account, it is critical to staying secure online. Tools like password managers can simplify keeping accounts and passwords organized, which can seem complex.
Joe’s security mistakes became far more severe when he moved his workday to the coffee shop. Sitting down at a central table ensured that his screen could be viewed by passersby and people sitting at nearby tables. Although most patrons don’t care about Joe’s work, one could be a malicious actor who will use their view of his screen to steal confidential information or record his login information for later.
The largest error Joe made was using the shop’s open internet network for his work without taking additional security steps. Such a network is unsecured, meaning that cyber threat actors can easily steal data being transmitted across it. This could include Joe’s login information and passwords, communications with other staff and the client, contact information, and, most importantly, login and financial information for the company’s accounts. This exposes company data and internal communications that should remain confidential. It allows hackers to steal money and otherwise manipulate the company's accounts.
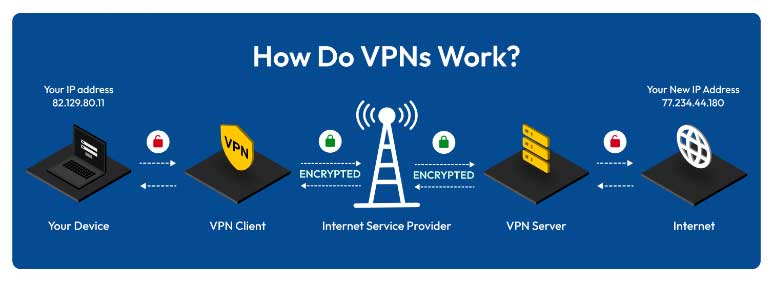
Avoiding using unsecured networks is the first step towards preventing data from being stolen. Even public internet networks with security and passwords can be a threat as they are often more weakly secured than private or company networks. A more secure solution is using a virtual private network (VPN). This creates a private network for your device when connected to another network, preventing your data from being exposed to other users on the network.
In all, Joe’s lack of knowledge and usage of cybersecurity best practices could have exposed his company to having its accounts hacked, communication compromised, and data, and money stolen.
The threats to remote workers like Joe are significant and rising. According to a report from Gitnux, 67 percent of companies have seen an increase in cyberattacks since transitioning to remote work. A Tenable study finds that remote workers are especially at risk, reporting that 67 percent of business-impacting cyberattacks targeted them. Additionally, Lookout finds that 92 percent of remote workers use personal devices for work and 42 percent have saved a work file to that device. If proper precautions are not taken, both these actions can lead to increased cybersecurity risks.
If you or your company want to learn how to stay secure while working remotely, CyberMontana offers Security Awareness Training (SAT) targeted to assist workers, businesses, and governments across Montana in developing the skills and knowledge to stay cyber secure, including while working from home. SAT is delivered through short, asynchronous, online lessons which offer critical cybersecurity information and interactive activities to test your knowledge. Each month brings new lessons on relevant cybersecurity topics. January focuses on staying secure while working from home and on ways to avoid mistakes similar to Joe's. This includes building strong passwords, best practices to prevent your screen from being read while working in public, and ways to select and use secure networks, including utilizing VPNs.
Take a free demo SAT lesson on working from home securely by clicking here. To learn more about using the program for your organization and to enroll, contact info@cybermontana.org.
